In today’s digital world, companies collect and store more customer data than ever before. This includes details like names, phone numbers, transaction history, and even personal identifiers. With rising cyber threats and privacy expectations, using the right Data Protection Techniques has become essential to keep this information safe and build customer trust.
Why Protecting Customer Information Matters
Customers expect businesses to keep their information secure. Any data leak can cause:
- Loss of customer trust
- Legal penalties
- Financial loss
- Damage to the company’s reputation
Strong Data Protection Techniques help prevent these risks by creating safe systems that protect sensitive information from unauthorized access.
1. Encryption for Secure Data Storage and Transfer
Encryption converts data into unreadable code unless someone has the proper key to unlock it. Companies should use encryption for:
- Stored files
- Database information
- Emails and messages
- Online transactions
This is one of the most effective Data Protection Techniques because even if data is stolen, it remains unusable.
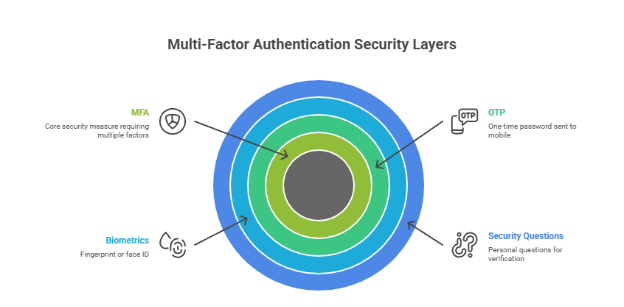
2. Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring more than just a password. It may include:
- OTP sent to mobile
- Fingerprint or face ID
- Security questions
This technique ensures that even if a password is compromised, the attacker cannot access sensitive data easily.
3. Regular Software Updates and Patch Management
Cyber attackers often look for weaknesses in outdated software. Companies must regularly update:
- Operating systems
- Security applications
- Browsers
- Company tools and platforms
Keeping everything updated is a simple yet powerful part of Data Protection Techniques.
4. Access Control Based on Roles
Not every employee needs access to all company information. Role-based access control helps:
- Limit who can view certain data
- Prevent accidental data misuse
- Reduce insider threats
This ensures that sensitive customer information is seen only by authorized team members.
5. Employee Training and Awareness
Many data breaches happen because of human mistakes. Companies should train employees about:
- Safe password handling
- Identifying phishing emails
- Secure browsing practices
- Handling customer data responsibly
Well-trained staff strengthens all other Data Protection Techniques and reduces everyday security risks.
6. Regular Data Backups
Backups protect companies during:
- System failures
- Ransomware attacks
- Accidental deletion
Storing backups in secure cloud locations or offline drives ensures that data can be restored quickly.
7. Monitoring and Detecting Unusual Activity
Companies should use automated tools to detect suspicious activity such as:
- Multiple login attempts
- Unknown IP addresses
- Sudden changes in system behavior
Continuous monitoring is one of the most essential Data Protection Techniques because it helps identify threats early.
With cyber threats increasing, companies must build strong systems to protect customer information. Using a combination of smart tools, trained employees, and reliable Data Protection Techniques, businesses can safeguard sensitive data and maintain customer trust. Strong protection today prevents major problems tomorrow.


